How is a Transaction Verified on a Cryptocurrency Network?
Cryptocurrencies, the digital assets based on blockchain technology, have gained significant traction in recent years. A core aspect of their functionality is the verification of transactions, ensuring security and integrity within the network. This article aims to explore the intricacies of how transactions on a cryptocurrency network are verified, as well as the fundamental processes and mechanisms involved.
The Basics of Cryptocurrency Transactions
In a cryptocurrency network, a transaction transfers value from one user to another. Each transaction is recorded on a public ledger known as the blockchain. For a transaction to be considered valid and included in the blockchain, it must undergo a verification process. The process ensures that the transaction is legitimate, preventing double-spending, in which a user attempts to spend the same cryptocurrency unit more than once.
Key Components of Transaction Verification
1. Digital Signatures and Public-Private Key Cryptography:
– When a user initiates a transaction, they sign it using their private key. This signature is unique to the transaction and the user’s private key, ensuring authenticity.
– The transaction also includes the user’s public key, allowing network participants to verify the signature. The public key serves as an address, enabling others to send cryptocurrency to the user.
– The digital signature ensures that only the rightful owner of the cryptocurrency can initiate a transaction, maintaining security.

2. Broadcasting the Transaction:
– Once signed, the transaction is broadcast to the network. For verification, it is sent to various nodes (computers connected to the cryptocurrency network).
– Nodes are essential in maintaining the decentralized nature of the network, as they collectively validate and record transactions.
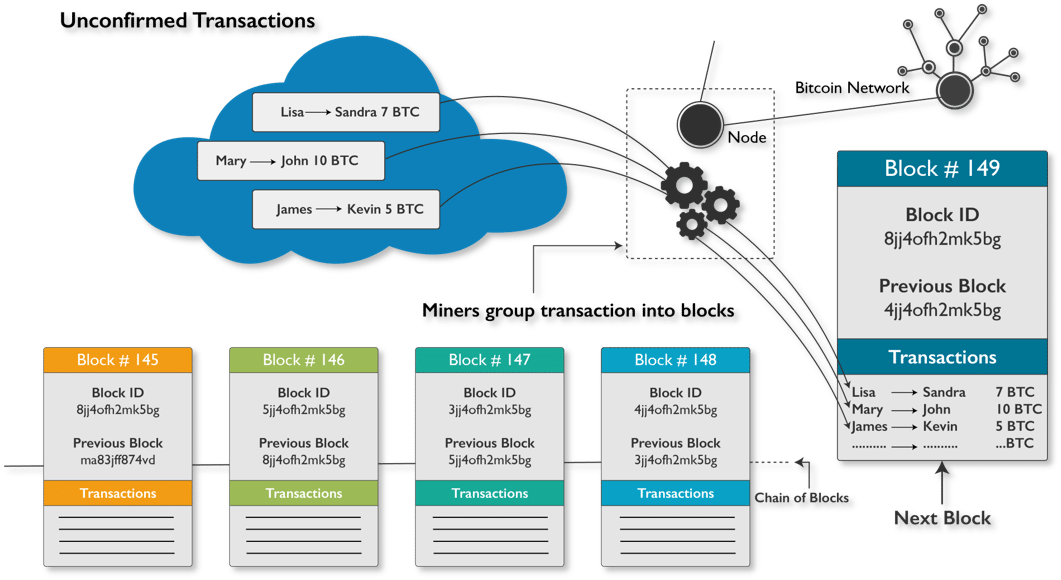
3. Validation by Nodes:
– Nodes verify the transaction against several criteria:
– Syntax and Format Check: Ensures that the transaction is correctly formatted and adheres to the protocol’s standards.
The Double-Spending Check ensures that the cryptocurrency being spent has not been spent before.
– Sufficient Funds Check: Verifies that the user has enough balance to complete the transaction.
– Once these checks are completed, nodes relay the validated transaction to other nodes, propagating it through the network.
4. Inclusion in a Block:
– Verified transactions are collected into a block by miners (in Proof-of-Work networks) or validators (in Proof-of-Stake networks).
– Miners or validators compete to add the next block to the blockchain. This competition involves solving complex cryptographic puzzles (Proof-of-Work) or being selected based on stake (Proof-of-Stake).
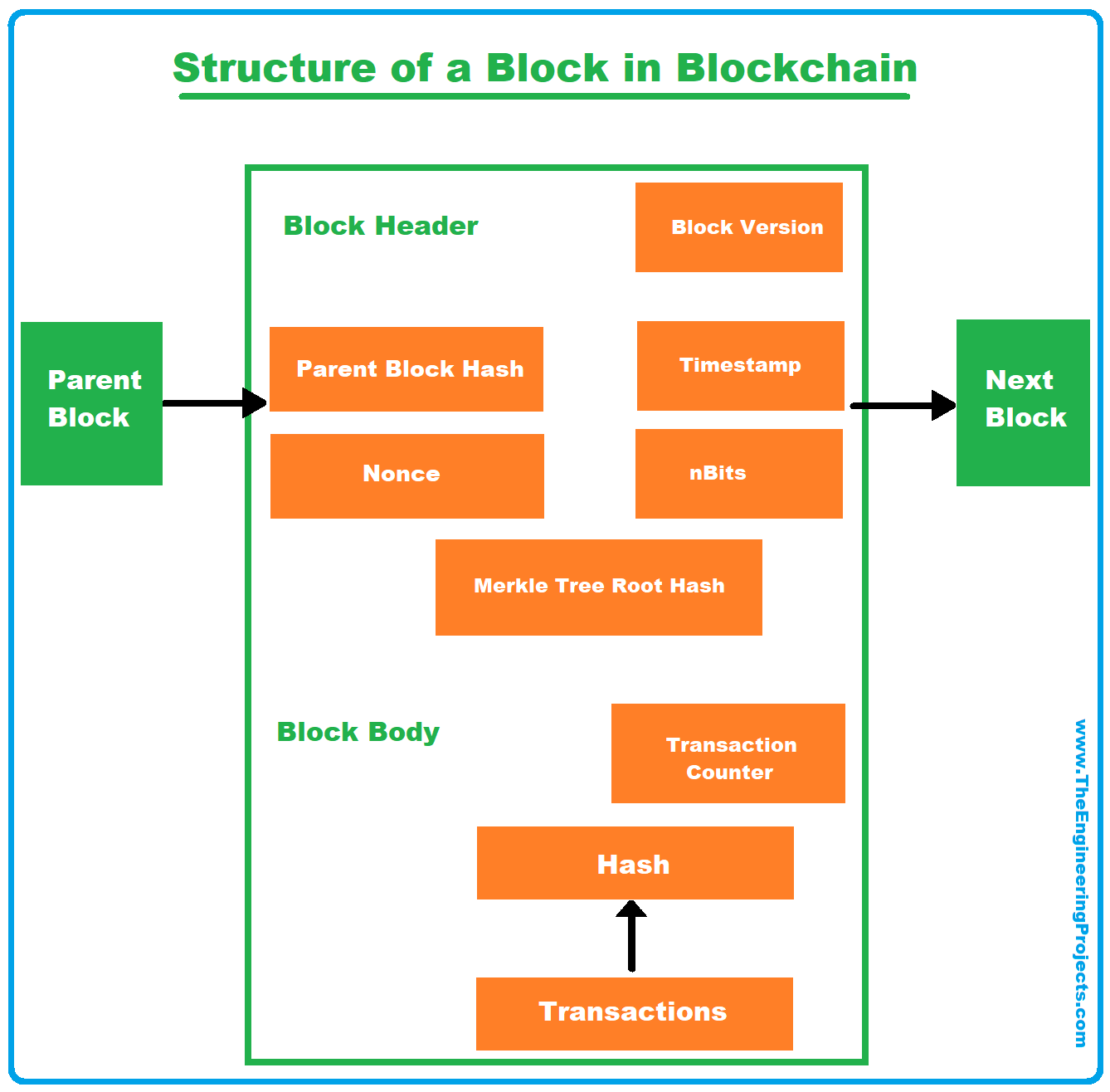
5. Consensus Mechanism:
– The network employs a consensus mechanism to agree on the validity of the new block.
– Proof-of-Work (PoW): Miners solve a cryptographic puzzle, and the first one to solve it gets to add the block to the blockchain. Other nodes must verify the solution to ensure that it meets the required difficulty.
– Proof-of-Stake (PoS): Validators are chosen to create new blocks based on the number of coins they hold and are willing to “stake” as collateral. This selection process is designed to be more energy-efficient than PoW.
– Once consensus is reached, the block is added to the blockchain, and the included transactions are considered confirmed.

6. Confirmation and Finality:
– A transaction is confirmed once it is included in a block. However, multiple confirmations (inclusion in subsequent blocks) increase the security of the transaction, making it more resistant to attacks.
– The number of confirmations required for a transaction to be considered final depends on the cryptocurrency network and the transaction amount. Confirmations are typically required for higher-value transactions.
Transaction verification on a cryptocurrency network is a multifaceted process involving digital signatures, broadcasting, validation by nodes, inclusion in a block, and consensus mechanisms. This process ensures the security and integrity of the blockchain, maintaining trust in the decentralized system. By understanding these steps, users can appreciate the robustness of the technology underpinning cryptocurrencies and their transactions.